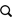Tips for Keeping Your Records and Business Safe from Ransomware
Are you aware that the greatest threat to your organization’s data security won’t steal a single bit of information from you? It’s a new trend in malicious software called Ransomware.
Ransomware, the fastest-growing threat to your network and data, doesn’t want to access your records at all; it wants to keep you from accessing them—until you fork over ransom money. You boot up your computer, type your password in the login screen and you’re alarmed to find that you’re denied access as surely as if someone had re-keyed the locks on the building overnight. Next comes a ransom “note” with instructions for regaining access to your files.
These viruses are spreading fast and new “strains” are cropping up faster than antivirus protections can keep up.
Ransomware Facts
- As noted by the FBI, ransomware is “an insidious type of malware that encrypts, or locks, valuable digital files and demands a ransom to release them.”
- AV-Test Institute, an independent cyber-security firm, reported there are “390,000 new malicious programs every day’”
- Anyone is fair game. Targets vary widely including, “hospitals, school districts, state and local governments, law enforcement agencies, small businesses, large businesses,” the FBI reported.
- Ransomware attacks are increasing. There has been a 300% rise in these attacks in 2016 with an average of 4,000 ransomware attacks occurring daily since January 1, 2016.
- Ransomware can leads to temporary or permanent loss of sensitive information, disruption of operations, and financial loss due to the expense to repair and restore systems or files.
- It can have a negative impact on reputation and cause customer distrust.
- Crypto ransomware encrypts certain files or data; locker ransomware can lock you out of the entire system or only specific components.
- Ransom demands are usually under $1000 because, according to the National Cybersecurity Institute, businesses are more likely to pay a smaller “nuisance” ransom so they can get back to work.
Ransomware M.O.
There are two primary ways in which a ransomware attack occurs. The first arrives via an innocuous-enough looking email. The user opens the email and clicks on a reasonable attachment such as an invoice, which subsequently deposits malicious software onto the computer that can quickly spread through a network. The second avenue of infection is more creative and no longer need you to click a link to infect your computer. According to FBI Cyber Division Assistant Director James Trainor, “They do this by seeding legitimate websites with malicious code, taking advantage of unpatched software on end-user computers,” he said in a recent FBI article. As cyber-criminals become more creative, businesses must become more vigilant.
Anatomy of a Ransomware Attack
A user likely won’t realize she is under a ransomware attack until a threatening screen appears. Some look like the common “blue screen of death” on a computer, others have a detailed ransom note, still others look like an official notice from a government agency as seen in the feature photo. In general, what they have in common is a “ransom” request instructing the user to pay a fee (usually in Bitcoin) to regain access to their files. Paying the ransom, however, doesn’t ensure restoration of the files.
Preventing Ransomware Attacks
- Multiple layers of security: The best way to prevent a ransomware attack is through multiple layers of security beginning with a good anti-virus/anti-malware program, followed up with web filtering and firewall protection. Utilize automatic updates, as anti-virus providers work continuously to combat new viruses and frequently push updates to protect your system.
- User awareness: The next layer of defense is user awareness. Make sure users verify the legitimacy of an email before they click a link or download any attachments. Cybercriminals have become smarter at both targeting specific markets and in the sophistication of language they use in their phishing emails. Better translations into the native language of the country in which they are attacking makes it easier for phishing emails to appear to be legitimate than in the past.
- Limited access: Limit user privileges to only those necessary to fulfill their role. Ransomware’s access follows the same path as the user’s privileges within the system.
- Backup: Ultimately, the most important step in mitigating ransomware attack focuses on recovery after an attack occurs. Make frequent backups of data and, when possible, house those files outside of the network, since certain families of malware can infiltrate the network, seek out and corrupt backups. Create “serialized” backups that keep generations of files, allowing restoration with an older incarnation of the files in case a more recent one has become corrupted.
What to do if Your Business is Attacked
Don’t panic. Alert your IT department, if you have one. They may have a specific protocol.
If you are the owner and IT department for your business, start by removing the infected computer from the network to keep the virus from spreading. Close the warning message window; you may want to screenshot or take a picture of it for future reference. Assess your system to determine which files have been encrypted, then restore your data.
There are different ways to restore data. If you can access a good restore point for the system, you can try restoring to a previous point in your computer’s history. Another option, if you have a good, recent backup of your data, is to perform a clean installation of your operating system and restore your data.
If you don’t feel qualified to do this troubleshooting on your own, you can always hire an IT expert to clean up and restore your system for you.
Do not pay the ransom. Despite the temptation to pay a ransom and move on with restoring and securing your data, security experts advise businesses that paying ransom simply funds R & D for cyber criminals and won’t unlock your files. Paying a ransom also adds your business to the list of easy targets.
You’ve gone to great length to protect your business investment: background checks and drug tests for employees, high-tech locks and security systems to protect their offices and top notch encryption of customer data. Don’t allow ransomware to padlock your business.
7 Effective Communication
Effective Communication Women Making History
Women Making History Grants & Funding Sources
Grants & Funding Sources Interview Prep
Interview Prep Impactful Leadership
Impactful Leadership Dressing for Work
Dressing for Work Dressing for Your Style
Dressing for Your Style Interview Style Tips
Interview Style Tips Women's Stocking Stuffers
Women's Stocking Stuffers Gift the Busy Traveler
Gift the Busy Traveler Airport Layover Activities
Airport Layover Activities Traveling & Eating Healthy
Traveling & Eating Healthy Travel Like a Boss Lady
Travel Like a Boss Lady The Dual California Life
The Dual California Life Gifts for Thanksgiving
Gifts for Thanksgiving Summer Reading List
Summer Reading List Top Leisurely Reads
Top Leisurely Reads New Year, New Books
New Year, New Books Life Lessons from a Sitcom
Life Lessons from a Sitcom Oprah, Amy or Amal?
Oprah, Amy or Amal?